ControlUp shared a simple bash script for checking the XZ Utils version on devices and determining if it is affected by CVE-2024-3094. Resources and further information on this topic were provided. The shared script also includes an event script for checking the version on devices. Some discussion and referenced sources were also provided. Find the script for checking for affected devices at https://x.com/wdormann/status/1774221251931742706?s=46&t=gdqbN_60lboMJbaqr16mcw. The index script can be found in the thread below the original post.
Read the entire ‘How to Check for Affected Devices with ControlUp’s Bash Script’ thread below:
Hey all, wrote a simple bash script for checking the version of you XZ Utils on your devices and output if it’s running a version that’s affected by the CVE listed below. More info on this here
This is the script for running it manually on a device, you can check the Device Events tab for the response. Feel free to adjust as needed
Updated script in thread below
I found this comment on Twitter which kinda makes sense not running the backdoored binary…
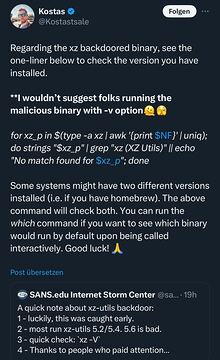
You’d think that xz –version or -V would not do more harm than the app being used, so it feels a bit overreacted. But I’ll see if the other one works well. So far my devices have been 5.2.5
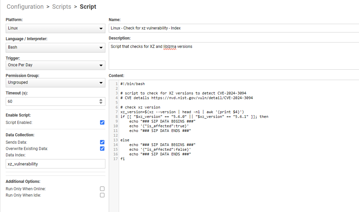
Here’s the script that drops it in an index (still with the –version checking).
Updated script in thread below
https://twitter.com/Malwar3Ninja/status/1774099755381170340?t=FDjI76n_CP9bplA0cxWulw&s=19
Guess there’s a few ways. Sigh. Back at it tomorrow
Yep. Its getting weird… Will Dormann mentioned another way to determine if the binary is malicious or not:
https://x.com/wdormann/status/1774221251931742706?s=46&t=gdqbN_60lboMJbaqr16mcw
Index script (updated for true/false case sensitivity):
“`#!/bin/bash
script to check for XZ versions to detect CVE-2024-3094
CVE details https://nvd.nist.gov/vuln/detail/CVE-2024-3094
check xz version
xz_version=$(strings which xz | grep "(XZ Utils" | head -n1 | awk ‘{print $4}’)
if [[ "$xz_version" == "5.6.0" || "$xz_version" == "5.6.1" ]]; then
echo "### SIP DATA BEGINS ###"
echo ‘{"is_affected":true}’
echo "### SIP DATA ENDS ###"
else
echo "### SIP DATA BEGINS ###"
echo ‘{"is_affected":false}’
echo "### SIP DATA ENDS ###"
fi“`
Event script:
“`#!/bin/bash
script to check for XZ versions to detect CVE-2024-3094
CVE details https://nvd.nist.gov/vuln/detail/CVE-2024-3094
check xz version
xz_version=$(strings which xz | grep "(XZ Utils" | head -n1 | awk ‘{print $4}’)
if [[ "$xz_version" == "5.6.0" || "$xz_version" == "5.6.1" ]]; then
echo "### SIP EVENT BEGINS ###"
echo "Device is affected"
echo "### SIP EVENT ENDS ###"
else
echo "### SIP EVENT BEGINS ###"
echo "Device is not affected"
echo "### SIP EVENT ENDS ###"
fi“`
Continue reading and comment on the thread ‘How to Check for Affected Devices with ControlUp’s Bash Script’. Not a member? Join Here!
Categories: All Archives, ControlUp for Desktops, ControlUp Scripts & Triggers
